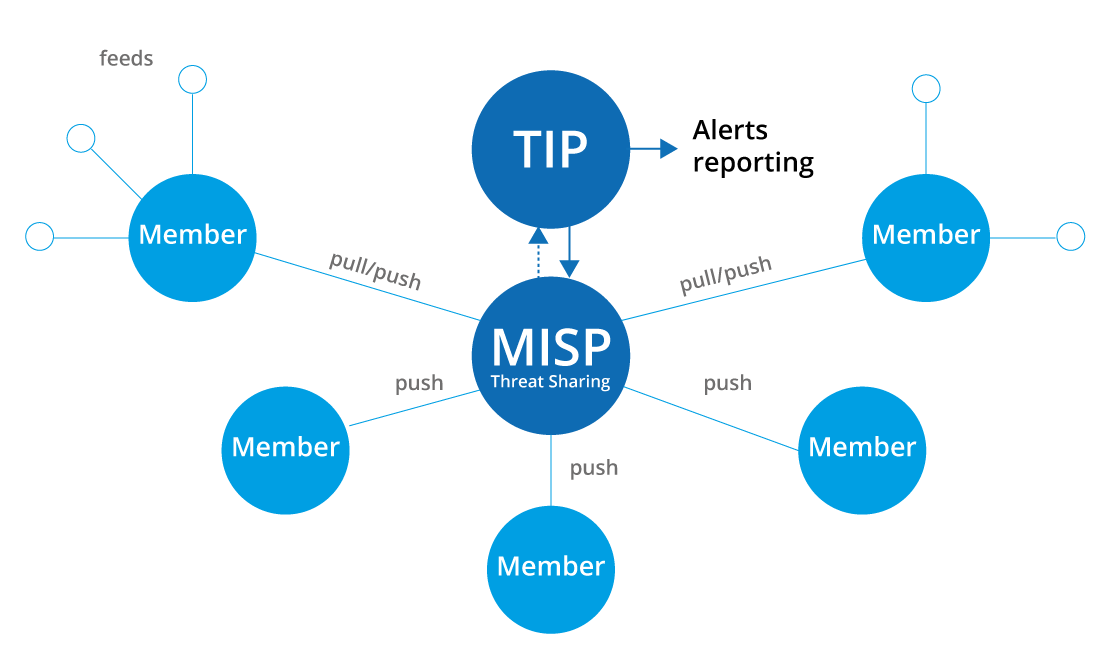
In Innovery, this process has been automated with the INNEW service, Innovery Early Warning, specifically designed to inform our customers about the potential vulnerabilities on their systems as quickly as possible, both related to CVEs and cyber threat intelligence feeds.
The service uses a variety of information feeds available from both public and commercial sources, including several privileged feeds that are not available elsewhere.
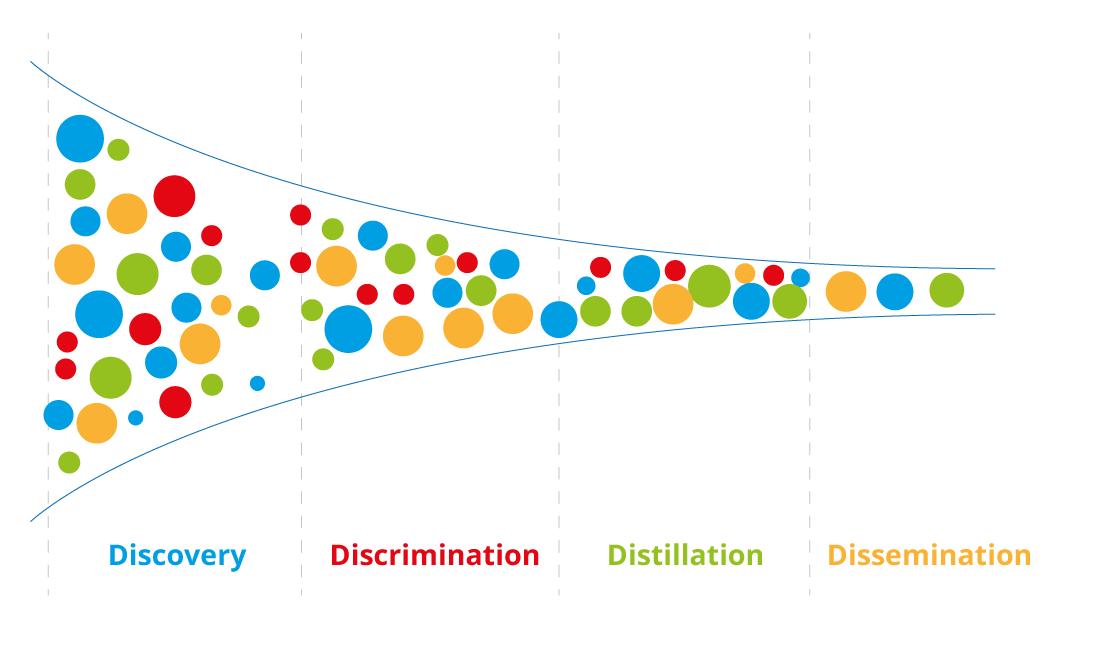
INNEW filters hundreds of events we receive each day and, using customers’ asset inventory, it matches those that are relevant to their infrastructure and promptly notifies them to contacts via reports/ emails and the Early Warning portal.
The service does not actively scan Client networks, so it is totally non-invasive, but it can be integrated with Continuous Vulnerability Management tools in order to improve the speed of threat response.
The service enables an effective collection, analysis, and sharing of information about critical vulnerabilities, in association with information about the involved technologies, the availability of exploits, and the existence of zero-day vulnerabilities together with the resulting level of risk.
Once the impact of the vulnerability is analyzed, clients are properly informed so that their systems can be kept up-to-date and monitored in order to check whether the vulnerability can be exploited.