A response plan that has not been tested is as useful as having no plan at all.
The midst of a cybersecurity incident is not a good time to test the plan.
Scenario-based testing of your cybersecurity incident response capability is a high-impact way of engaging your response teams (which includes executive leadership and not just the IT team) in the business decision-making process, that goes with reacting to a critical incident. Regular testing of your response plans will help everyone involved to be familiar with the process and prepare them to react when a critical incident occurs.
The focus is no longer prevention: you can’t stop attacks. It’s now about better detection and readiness for the inevitable in order to survive in today’s complex world.
The Cyber Security Due Diligence is a cyber security service which aims to discover any valuable assets, apps, accounts, and points of presence that reside on digital channels and remain susceptible to all types of attack and abuse.
In order to provide an effective and reliable Cyber Security Due Diligence, Innovery Group makes use of bespoke OSINT tools and third-party commercial sources empowered by the cyber security skills of its team.
Approach and Methodology
The Cyber Security Due Diligence consists of the following activities:
- Leaked credentials collection and credentials stuffing
- Data breach investigation
- Domain Typosquatting check
- Deep and Dark Web investigation
- Social Media monitoring (SMM)
- Vulnerability Assessment OSINT-based
Deliverables
Innovery Group will provide one technical report for the Cyber Security Due Diligence at the end of the engagement. The technical report will include detailed technical analysis along with the recommendations and remediations.
A score will be calculated by the vulnerabilities/alerts’ amount and severity and will reflect the digital cyber risk status of your company.
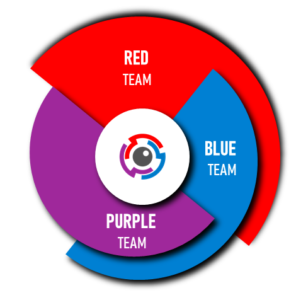
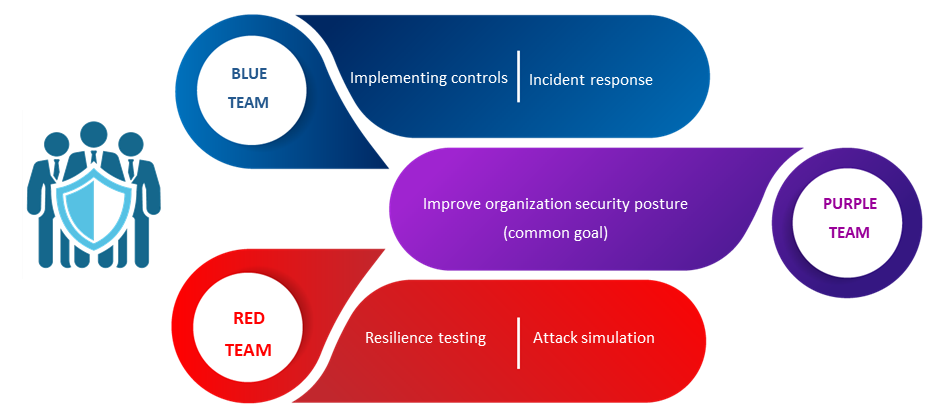
Team-oriented security testing activities are aimed to strengthen an organization’s security by learning from the ensuing combat. The operations are carried out by three teams: Red, Blue and Purple Teams. The Red team exists to attack, the Blue one to defend, while the Purple team is intended to facilitate the integration between the two groups.
Red Team (Attackers) is dedicated to testing the effectiveness of a security program by emulating the tools and techniques of likely attackers in the most realistic way possible.
Blue Team (Defenders) refer to the internal security team that defends against both real attackers and Red Teams.
Purple Team (Defender learns from Attacker) integrates the defensive tactics and controls from the Blue Team with the threats and vulnerabilities found by the Red Team.
Approach and Methodology
RTT exercises simulate real-world attacks against an organization, challenging its security practices and controls to identify gaps that are not readily apparent from conducting standard assessments.
Red Team Testing key elements:
- Goal-oriented, rather than scope-oriented
- Assess both people, process and technology
Make use of bespoke tactics, techniques and procedures
From the initial recon to the mission accomplished, RTT consists of six steps where each of them is the prerequisite for the next one:
- Reconnaissance
- Initial compromise
- Privilege escalation
- Maintain presence
- Target identification
- Mission complete
Deliverables
The RTT Report details each phase highlighting the attacker TTPs, malware IOCs and GDPR compliance issues.
Approach and Methodology
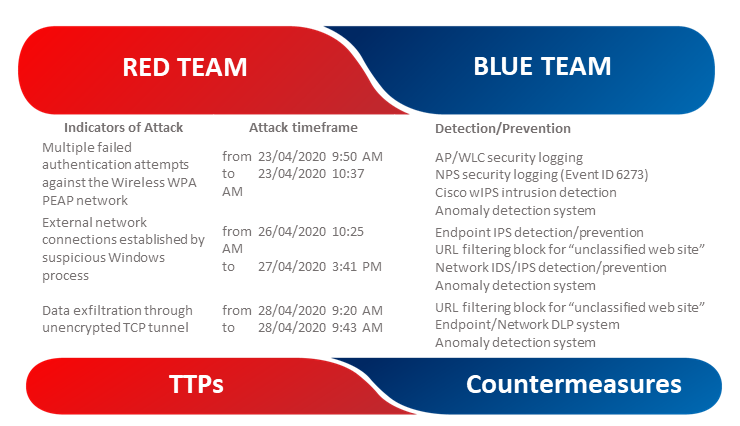
The Attacks&Countermeasures table highlights the Tactics, Techniques and Procedures (TTPs) used by the RTT team along with the Countermeasures to be implemented by the Blue Team.
Execute a post-mortem/retrospective analysis at the end of the RTT is strongly recommended. In order to support this activity, all the IOCs related to any of the malwares and backdoors produced and engaged during the attack are reported.
Approach and Methodology
PTT is an open engagement where the attack activity is exposed and explained to the Blue Team as it occurs. Purple Team Tests are “hands-on keyboard” exercises where Red and Blue teams work together with an open discussion about each attack technique and defense expectation to improve people, process, and technology in real-time.
Purple Team Testing key elements:
- Strategy-oriented, rather than scope-oriented
- Assess both people, process and technology
- Make use of bespoke tactics, techniques and procedures